The Dashboard page includes sections with filters to track pending
status items by type, and quick links out to requests and engagements saved in the
application.
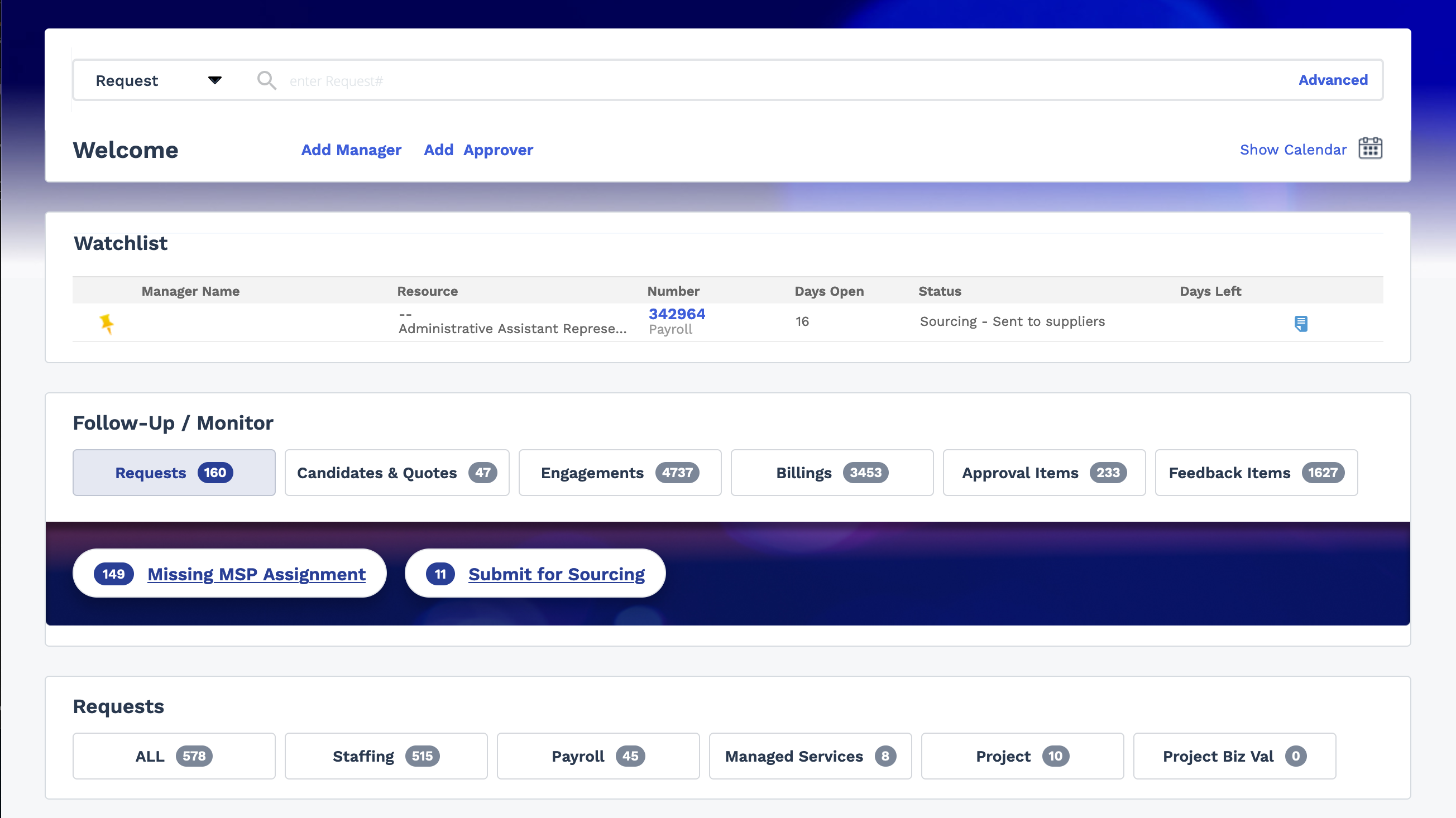
The page is organized into a
Watchlist,
Upcoming
Events,
Follow-Up/Monitor,
Requests,
Engagements, and
Broadcast Reminders sections, allowing you to locate items
that require action or review. The
Watchlist section displays
items that you have added to your watchlist. You can also click the links at the top of
the page to the right of your name to complete the following tasks:
All buttons (
) and filter pills (

display counts next to the label, giving you a quick view
of the number of items with this status. Clicking a filter pill takes you to the page
with the item, for example, the
Requests page. When a particular
button or filter pill does not have any action items (the count is '0'), it does not
appear on the
Dashboard page view.
Note: The filters
on the Upcoming Events section are saved and reloaded
automatically. If you create filters, and leave the page, when you return, you
configuration is automatically loaded until you modify it.
The Follow-Up/Monitor section displays items that you
are required to view, or items that you are assigned to. Clicking each category in the
top row displays pills with items in a specific reason that is relevant to the category.
For example, clicking the Engagements button displays pills for
'Pending MSP Fill' and 'Financials Required'. You can also filter by the MSP contact on
the request.
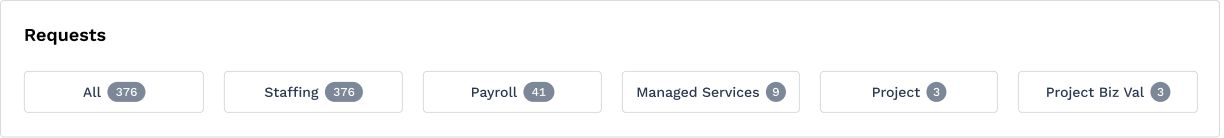
The Requests and Engagement sections
display buttons related to the service types enabled for the client organization.
Clicking each button navigates you to the page.
In addition to the action overview, you can also set up a
request in this view. Click  populate basic job information. For more
information about opening requests, see Quick Create Request.
populate basic job information. For more
information about opening requests, see Quick Create Request.
Note: If the Bring Your Own Key (BYOK) data encryption feature is enabled, some fields in the application do not off 'like' suggestions. For example, if you are adding a user name to a field, you can type in a few characters and the application searches available data to suggest existing name values. With encryption, you need to provide the exact name value because the system cannot search encrypted values. It is suggested that if you have the value, copy/paste it into the data field.
For more information about data encryption, see Bring Your Own Key Encryption.


![]() populate basic job information. For more
information about opening requests, see Quick Create Request.
populate basic job information. For more
information about opening requests, see Quick Create Request.